Cross-Site Scripting (XSS)
| Risk Factor | 4/5 |
|---|---|
| Exploitability | 4/5 |
| Prevalence | 5/5 |
| Impact | 3/5 |
| Detectability | 4/5 |
Cross-Site Scripting (XSS) allows an unauthenticated attacker to steal information from website.
Based on: web application that reflects user’s input to the attacker.
TL;DR: Sending scripting code to WebApp & get back data.
It allows an unauthenticated attacker to run scripts in the context of user’s browser to:
- steal confidential information.
- perform actions on behalf of the user.
- view information that the user can view.
- initiate interactions with other application users, including malicious attack, that will appear to originate from the victim user.
- deny availability.
Types of XSS
- Reflected XSS.
- Stored/Persistent XSS.
- DOM based XSS.
1. Reflected XSS
- The most common type.
- Requires the victim to take action such as clicking the crafted URL (or convince the victim to input data in the browser console)
- Delivered via tricking user to click URL.
- The attack is delivered & executed via a single request and response.
- CVSS Score: 5.4 (CVSS:3.1/AV:N/AC:L/PR:L/UI:R/S:C/C:L/I:L/A:N)
Walkthrough
- victim
- ..
2. Stored/Persistent XSS
- The most dangerous of XSS as the payload is permanently stored in the WebApp.
- To resolve it, it is not sufficient to fix the vulnerability, but also it needs to purge the stored XSS codes that have been “planted”.
- CVSS Score: 8.8 (CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H)
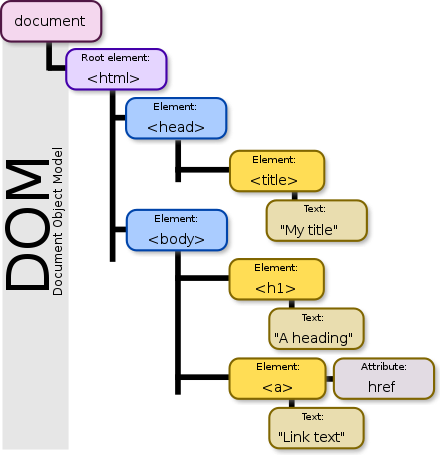
3. DOM based XSS
AKA client side XSS, JavaScript is taking some data from the user and mishandling it in some way that allows us to execute JavaScript.
DOM XSS (type-0 XSS) is a vulnerability that appears in the DOM (Document Object Model) instead of part of the HTML.
In the stored or reflective XSS, we can see the vulnerable payload in the response page, whereas in the DOM based XSS, the HMTL source code of the attack will be exactly the same, it can only be observed on runtime or by investigating the DOM of the page.
TL;DR: the difference
Stored/Reflected XSS: the attack payload is placed in the response page.
VS
DOM XSS: The page itself (the HTTP response) does not change, but the client side code contained int he page execute differently due to the malicious modification that have occured in the DOM enviroment. The attack payload is executed as a result of modifying the DOM “enviroment” in the victim’s browser used by the original client side script, so the client side code runs in an “unexpected” manner.
The payload is executed as result of modifying the DOM “environment” within the victim’s browser used by the original client side script, so that the client side code runs in an “unexpected” manner.
Note from wiki: Document Object Model (DOM) is a cross-platform and language-independent interface that treats an XML or HTML document as a tree structure wherein each node is an object representing a part of the document. The DOM represents a document with a logical tree. Each branch of the tree ends in a node, and each node contains objects. DOM methods allow programmatic access to the tree; with them one can change the structure, style or content of a document.