Cyber Kill Chain
“Kill chain” was originally used as a military concept related to the structure of an attack.
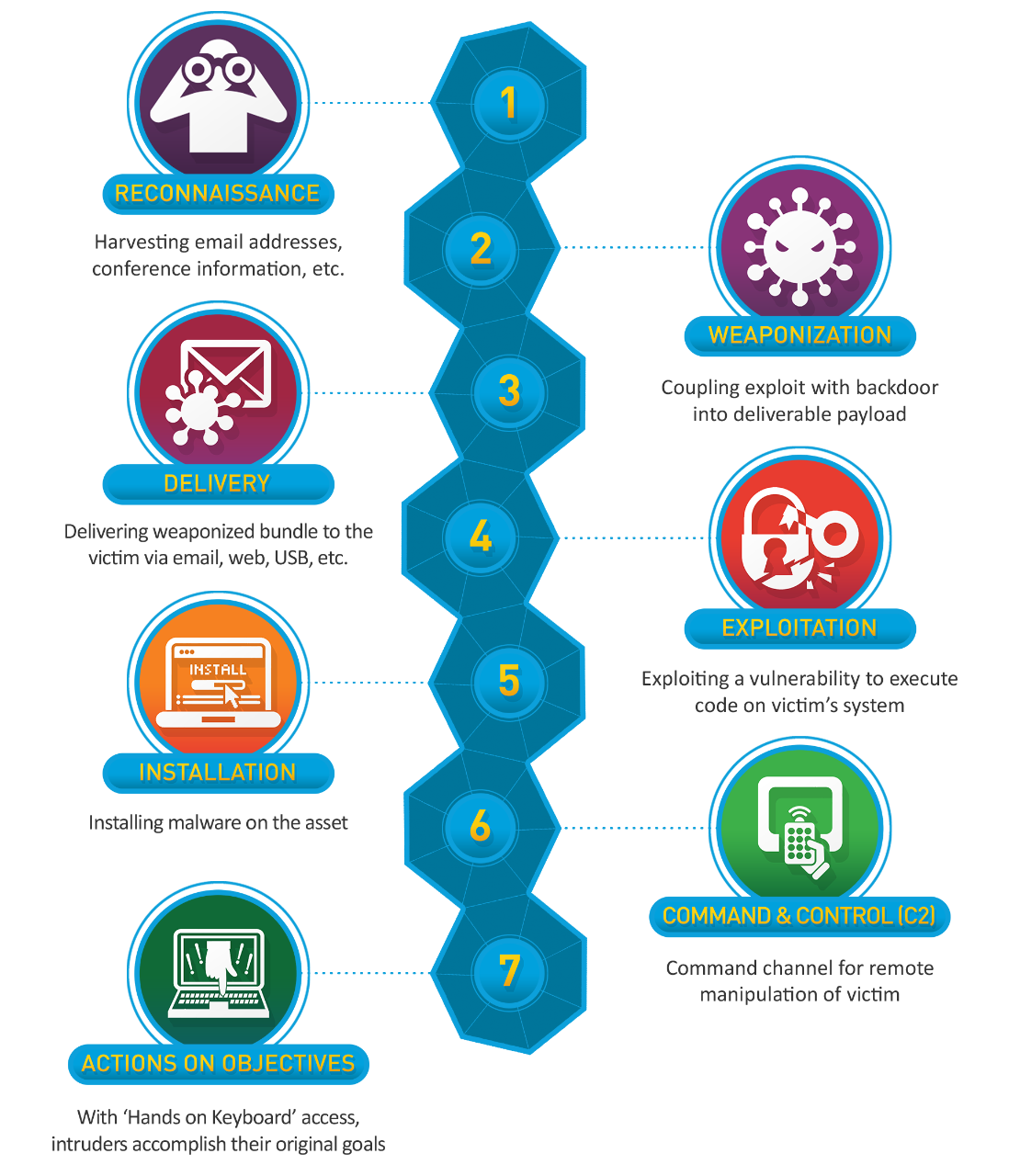
Many moons ago Lockheed-Martin popularize the concept of the Cyber Kill Chain® framework as threat assessment model and prevention tool:
| Stage | Cyber Kill Chain® | mnemonic | Notes | Mitigation |
|---|---|---|---|---|
| 1 | Reconnaissance | Really | Gather information before the actual attack | Prevent attacker to gather information |
| 2 | Weaponization | Why | Preparing the attack tailored for the victim | Have security posture put in place in optimum level |
| 3 | Delivery | Does | Transmisiton of the weapon | Put in place various layer of protection |
| 4 | Exploitation | Everyone | Trigger the exploit | Always has the latest security update & extra layer of security, i.e. AV, NG-AV, HIDS, etc. |
| 5 | Installation | Involve | Install backdoor | Tripwire or some sort |
| 6 | Commmand & Control (C2) | Corruption | Communicate with attacker | Proper network analysist to block C2, network analitics, ex: ExtraHop |
| 7 | Actions objectives (AoO) | Always | Objective achieved & extrafiltration or data destruction | Pray, Legal & Insurance :-B |
On each stage, the blue team should put actions to:
- Detect
- Deny: prevent information disclosure,
- Disrupt
- Degrade
- Deceive
- Contain
the attacks.
MITRE maintains a kill chain framework expanding the Lockheed-Martin’s concept of Cyber Kill Chain®: MITRE ATT&CK® is an awesome website with free information for all.